Contents
Duo adds two-factor authentication to OWA logins, offering inline self-service enrollment and authentication with Duo Universal Prompt.
Does Duo for Microsoft OWA support the Duo Universal Prompt?
Yes, as of version 2.0.0 for Exchange 2013 and later on Windows 2016 and later. Please see the update instructions to install the latest version with Universal Prompt support, and then once you authenticate to Duo using the updated application you can activate the Universal Prompt experience for your users.
Which Windows and Exchange versions does Duo for Outlook Web Access support?
Duo supports Exchange 2013 and later installations on Windows Server 2016 and later.
Duo will support Windows Server 2025 in a forthcoming release.
Duo's last day of support for OWA 2010 was February 15, 2021. Microsoft Exchange 2010 reached the end of support on October 13, 2020.
Microsoft ended support for Windows Server 2012 and 2012 R2 on October 10, 2023.
Microsoft ended support for Windows Server 2008 and 2008 R2 on January 14, 2020.
Duo's last day of support for installation and use of any Duo applications on Windows operating systems or with Microsoft applications corresponds with the Microsoft end of support. We strongly urge you to upgrade to current versions of Microsoft operating systems and applications.
Can I silently install Duo for OWA from a command line or PowerShell?
Enter the following command into PowerShell or a Command Prompt to silently install Duo for OWA with default options (note that the MSI filename changes to reflect the version):
v2.0.0 and later:
msiexec.exe /i duo-owa-2.0.0.msi DUO_CLIENT_ID="DIDIXXXXXXXXXXXXXXXXXXXX" DUO_CLIENT_SECRET="xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" DUO_HOST="api-xxxxxxxx.duosecurity.com" DUO_AKEY="xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" /qn
Up to v1.3.3:
msiexec.exe /i duo-owa-1.3.2.msi DUO_IKEY="DIDIXXXXXXXXXXXXXXXXXXXX" DUO_SKEY="xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" DUO_HOST="api-xxxxxxxx.duosecurity.com" DUO_AKEY="xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" /qn
The parameter names passed to the installer (DUO_CLIENT_ID, DUO_CLIENT_SECRET, DUO_IKEY, DUO_SKEY, DUO_HOST, etc.) are case-sensitive!
You can also choose to change the default settings for fail mode to fail closed with FAILOPEN="#0", specify UPN as the username format sent to Duo instead of the sAMAccountName with DUO_USEUPNUSERNAME="#1", or define a shared session key on multiple OWA servers with DUO_AKEY="xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" (The AKEY is a string that you generate and keep secret from Duo; it should be at least 40 characters long.).
Can I silently uninstall Duo for OWA from a command line or PowerShell?
To silently remove Duo for Windows Logon from your environment, run the following command from PowerShell or an elevated command prompt, specifying the MSI file for the version of Duo for OWA currently installed:
msiexec.exe /x duo-owa-2.0.0.msi /qb
Which TLS versions does Duo for OWA support?
Duo for OWA 2.0.0 supports TLS 1.2 and greater.
Duo for OWA 1.3.2 and 1.3.3 support TLS 1.0 and greater.
Why do I receive an error when installing Duo for OWA 1.3.2 or 1.3.3 on Exchange 2013+ stating that .NET Runtime v2.0 is detected?
Duo is committed to ensuring our products adhere to the latest security recommendations. Microsoft recommends disabling TLS 1.0 & TLS 1.1 due to risk of potential security vulnerabilities. Learn more about Microsoft's position on TLS 1.0 and 1.1 in the white paper Solving the TLS 1.0 Problem.
As a result, Duo for Outlook Web Access (OWA) 1.3.2 and 1.3.3 on Exchange 2013 and later require .NET 4.5 or later present before installation to support TLS 1.2.
Updated .NET Minimum Requirements for OWA:
- .NET Runtime 4.5 or later
- ASP.NET 4.5 for IIS or later
Duo also requires the "IIS Management Scripts and Tool" feature for installation.
The PowerShell commands for installing these features are:
Import-Module ServerManager
Add-WindowsFeature NET-Framework-45-Features
Add-WindowsFeature NET-Framework-45-ASPNET
Add-WindowsFeature NET-WCF-HTTP-Activation45
Add-WindowsFeature Web-Scripting-Tools
Additionally, these OWA-related IIS application pools must use .NET v4.0.30319 or later.
- DefaultAppPool
- MSExchangeECPAppPool
- MSExchangeOWAAppPool
Typically no changes are needed to the IIS application pools. However, if you changed your OWA app pool settings from the Exchange defaults in the past you may need to adjust your pool .NET settings before installing Duo. You can change this from IIS Manager if necessary:
- Launch IIS Manager on your Exchange server.
- Navigate to Your IIS Server Name → Application Pools.
- Double-click the DefaultAppPool in the list to view basic settings.
- If the .NET drop-down version indicates v2.0, then change it to the V4.0 option. If you don't see the v4.0 option, did you install .NET 4.5 yet?
- Repeat this for the MSExchangeECPAppPool and MSExchangeOWAAppPool pools.
As of v2.0.0 Duo for OWA requires .NET framework 4.7.1 or later, and does not require ASP.NET 4.5 for IIS or the "IIS Management Scripts and Tool" feature.
Can I use TLS 1.1 or 1.2 with Duo on Exchange 2010?
TLS 1.1 and TLS 1.2 are not supported by Duo for OWA on Exchange 2010 due to limitations with Exchange Server 2010 and .NET Framework 3.5. Use TLS 1.0.
Duo's last day of support for OWA 2010 was February 15, 2021. Microsoft Exchange 2010 reached the end of support on October 13, 2020.
Consider migrating your organization to a later Exchange version to gain enhanced TLS compatibility, as well as numerous security and usability improvements.
Where should I install Duo Security if I have multiple Microsoft Exchange servers?
Install Duo Security's OWA application on the Microsoft Exchange server(s) that have the "Client Access Server role" or "Client Access services" installed. Other Exchange roles (like the Mailbox role) may also be present. We recommend installing Duo on the outermost client access servers.
Does Duo also protect ECP web access?
Yes, client access of the ECP web site will also require Duo authentication. If you already completed Duo authentication when logging on to your mailbox, you will not see an additional Duo prompt when accessing ECP settings.
Does Duo Security's OWA application affect login experience for Outlook Anywhere users?
Outlook Anywhere (also known as RPC over HTTPS) continues to work as it did prior to installing Duo. Duo's OWA application does not add two-factor authentication to the RPC endpoint. Outlook clients will not see an MFA prompt. We recommend against exposing the Outlook Anywhere endpoint to external access.
Does Duo Security's OWA application affect ActiveSync?
ActiveSync continues to work as it did prior to installing Duo. Duo's OWA application does not add two-factor authentication to the EWS and ActiveSync endpoints. ActiveSync clients will not see an MFA prompt. We do not recommend exposing the ActiveSync endpoint to external access.
Is Exchange 2016 supported?
Yes, as of version 1.2.0.
Is Exchange 2019 supported?
Yes, as of version 1.3.2.
Why did Duo stop working after I installed an Exchange Cumulative Update (CU)?
Installing Duo's protection for OWA modifies some of Exchange's XML application configuration files. Exchange 2010 and 2013 CU installers overwrite any customizations to the XML files (see Microsoft TechNet for details). Remove and reinstall the Duo application after the CU install is completed.
This issue with overwriting the XML configuration files during CU install was corrected in Exchange 2016 CU 1, but has been observed again in later cumulative updates. Therefore, we recommend always uninstalling Duo for OWA before applying any CU and reinstalling Duo for OWA after CU install success.
How can I configure the Duo fail mode for OWA?
If the Bypass Duo authentication when offline box is selected during installation, authentication attempts "fail open" after primary authentication is successful if the Duo service cannot be contacted. If you leave that option unchecked during install, Duo for OWA logins "fail closed", blocking OWA access if there is a problem contacting the Duo service.
Duo for OWA v1.x installers enabled fail open by default. Duo for OWA v2.x installers now default to fail closed for new installs and upgrades from v1.x, but upgrades from v2.0.0 to later releases preserve the installed fail mode selection.
This setting is controlled by a Registry DWORD value FailOpen, with 1 allowing fail open and 0 preventing fail open.
To change the fail mode:
-
Launch the Registry Editor (regedit.exe) as an administrator.
-
Locate the registry REG_DWORD value
FailOpenand change the current value to 0 or 1 as desired.Duo OWA Version Registry Path 1.x.x HKLM\SOFTWARE\Duo Security\DuoIis\FailOpen2.0.0+ HKLM\Software\Duo Security\DuoOwa\FailOpenAlternatively, you can enter the command
reg add "HKLM\Software\Duo Security\DuoOwa" /v FailOpen /t REG_DWORD /d 1 /fin PowerShell to create or update the registry value for "fail open" (substituting0for1to "fail closed"). -
After changing this setting restart the IIS server with
iisreset.
How do I enable Duo debug logging?
When troubleshooting an issue with OWA logins Duo support may request debug output from our application. You can enable this via a new registry value.
To turn on debug logging:
-
Launch the Registry Editor (regedit.exe) as an administrator.
-
Create a registry REG_DWORD value
Debugset to 1.Duo OWA Version Registry Path 1.x.x HKLM\Software\Duo Security\DuoIis\Debug2.0.0+ HKLM\Software\Duo Security\DuoOwa\DebugAlternatively, you can enter the command
reg add "HKLM\Software\Duo Security\DuoOwa" /v Debug /t REG_DWORD /d 1 /fin PowerShell to create or update the registry value. -
After changing this setting restart the IIS server with
iisreset.
Events are written as entries in the "Duo IIS Integration" event log under "Applications and Services Logs" in the Event Viewer.
To disable debug logging, set the Debug value to 0, or delete it entirely. Perform another iisreset to apply the change.
How do I change the username format sent to Duo?
Duo for OWA sends a user's sAMAccountName to Duo as the Duo username by default. You can change the username format sent to Duo to userPrincipalName (UPN) starting with version 1.3.2.
For this to work, OWA and ECP must be using Forms-Based Authentication (FBA). Learn how to enable FBA for Exchange 2010, 2013, and 2016 at Microsoft TechNet.
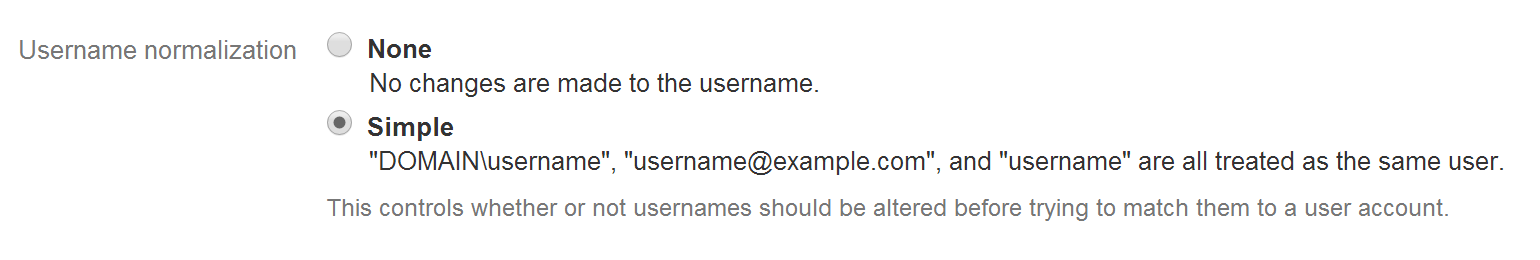
If you enable this option, you must also change the properties of your OWA application in the Duo Admin Panel to change the "Username normalization" setting to None, or Duo will drop the domain suffix from the username sent from OWA to our service, which may cause user mismatches or duplicate enrollment.
Choose to send userPrincipalName usernames to Duo during installation by selecting the Send username to Duo in UPN format box in the Duo installer.
Enabling this setting after Duo installation requires creating a new registry value.
To change the username format to UPN:
-
Launch the Registry Editor (regedit.exe) as an administrator.
-
Create a registry REG_DWORD value
UseUpnUsernameset to 1 to enable UPN username format.Duo OWA Version Registry Path 1.x.x HKLM\Software\Duo Security\DuoIis\UseUpnUsername2.0.0+ HKLM\Software\Duo Security\DuoOwa\UseUpnUsernameAlternatively, you can enter the command
reg add "HKLM\Software\Duo Security\DuoOwa" /v UseUpnUsername /t REG_DWORD /d 1 /fin PowerShell to create or update the registry value. -
After changing this setting restart the IIS server with
iisreset.
If you installed Duo on multiple Exchange servers be sure to make the same registry change on each server.
Can I use OWA monitoring tools like SCOM or the Test-OWAConnectivity cmdlet after Duo is installed?
Yes! If using Duo 1.2.x and earlier, first create a dedicated monitoring user account and mailbox (this is easily accomplished with Exchange's new-TestCasconnectivityUser.ps1 PowerShell script). Next, add that monitoring user to Duo and set that user's status to Bypass. There is no need to activate a device for the monitoring user.
With Duo OWA v1.3.2 and later, you do not need to create the Exchange health mailboxes as Duo users as we bypass 2FA for them automatically.
Why does the Duo installer exit with the error "No Exchange Server 2010 / 2013 Installation Detected"?
Ensure that you are installing Duo on an Exchange server that holds the Client Access Server role. Additionally, make sure to run the Duo MSI install package from an elevated command prompt (right-click and run as administrator).
Is SSL Offloading supported?
Duo's application for OWA supports SSL offloading for Exchange 2010, 2013, and 2016 starting with version 1.2.0.
Prerequisites:
- You must have your load balancer solution with SSL offloading in place.
- Your load balancer should have persistence configured to ensure that authentication requests for a user go to the same server.
- You must configure your load balancer to include the
X-Forwarded-ProtoandX-Forwarded-Forheaders in HTTP requests to your Exchange CAS role servers. Consult your load balancing solution vendor for instructions. - You must have disabled the HTTPS requirement on the OWA and ECP sites on your Exchange CAS role servers. Refer to instructions for Exchange 2013/2016 and Exchange 2010 at Microsoft TechNet.
- You must have enabled the "SSLOffloaded" setting in Exchange 2010 for the OWA and ECP sites via the registry editor. See Microsoft TechNet for complete instructions.
Verify that HTTP access to OWA and ECP sites works before installing Duo.
Once you install Duo for OWA make the following registry changes in order to permit HTTP requests from your load balancer:
- Open the registry editor (regedit.exe) on the Exchange CAS where you installed Duo.
- Navigate to HKLM\Software\Duo Security\DuoOwa (Duo v2.x) or HKLM\Software\Duo Security\DuoIis (Duo v1.x).
- Create a new DWORD (32-bit) value under DuoOwa or DuoIis called PermitInsecureRequests and set to 1.
- Create a new key under DuoOwa or DuoIis called InsecureHostList.
- Create a new String value under the InsecureHostList key called Host0 and set it to either the hostname or IP address of your load balancer (match this value to whichever your load balancer uses to identify itself to your Exchange server). Repeat host value creation (Host1, Host2, etc.) as necessary if incoming HTTP requests will be sent to OWA/ECP from multiple appliances.
- Close the registry editor.
- Open an elevated command prompt (right-click "Command Prompt" and select the "Run as Administrator" option) and run the
iisresetcommand.
You'll also need to disable the SSL requirement for the Duo IIS virtual directory (just like you did earlier for OWA and ECP).
- Open the Internet Information Services (IIS) Manager on the server(s) where you installed Duo for OWA.
- Navigate through the tree to Your Server Name → Sites → Default Web Site → duo.
- From the "duo HOME" view, double-click SSL Settings.
- Uncheck the Require SSL box and click Apply on the far right.
- Open an elevated command prompt (right-click "Command Prompt" and select the "Run as Administrator" option) and run the
iisresetcommand.
Finally, if you have any content switching rules or other configuration on your load balancer that allows explicit access to the /owa and /ecp virtual sites on your CAS hosts, update these rules to allow access to the /duo virtual site created by the Duo for OWA installer. If you configured the rule that sends the required X-Forwarded-Proto and X-Forwarded-For headers only for the /owa and /ecp virtual sites you may also need to add a similar rule for the new /duo virtual site. Consult your load balancing solution vendor for instructions.
Any errors generated by Duo for SSL offloading (such as missing X-Forwarded-Proto header or permitted host IP or name not found in registry) are written to the Windows Application log.
Possible errors and resolutions:
Duo authentication cannot accept a cleartext (http) connection: Verify that the PermitInsecureRequests registry value exists and is set to 1 (true) and that you raniisresetafter the registry edits.Rejecting cleartext request from hostname due to lack of x-forwarded-for: Verify that your load balancer is sending the X-Forwarded-For header to the CAS server.Rejecting cleartext request from hostname due to lack of correct x-forwarded-proto: Verify that your load balancer is sending the X-Forwarded-Proto header to the CAS server.Rejecting cleartext request from untrusted machine hostname: Verify that the host name or IP reported in the error has been added as a String value under the InsecureHostList registry key and that you raniisresetafter the registry edits.
Are Exchange hybrid deployments supported?
Duo protection for Outlook Web App doesn't extend to Office 365 or Exchange Online mailbox logons. To require Duo 2FA for Exchange Online access you may deploy one of Duo's solutions for Office 365 access. Configure a Remembered Devices policy "for all protected web applications" and apply it to both your OWA and Office 365 Duo applications to avoid multiple Duo authentication prompts when redirected from Exchange to Office 365 and vice-versa.
Is the OWA for iOS app supported?
No, the OWA app for iOS does not support multifactor authentication. Microsoft retired the OWA mobile apps on May 15, 2018. The native mail app for iOS will still work after Duo for OWA installation, providing mailbox access without MFA.
I upgraded my Duo install to 1.1.1 from an earlier version. Why are all my users now prompted to re-enroll with Duo?
The username normalization setting was moved from a checkbox in the OWA MSI installer to an application option in the Duo Admin Panel starting with version 1.1.1 of Duo for OWA. If you are upgrading from an older version of Duo's OWA application to 1.1.1 or later, login to the Duo Admin Panel and ensure that you have username normalization set to Simple in the properties of your OWA application.
Are Microsoft Small Business Server or Windows Server Essentials supported?
We do not test integration with SBS or Server Essentials and cannot guarantee support for those platforms.
Additional Troubleshooting
Need more help? Try searching our OWA Knowledge Base articles or Community discussions. For further assistance, contact Support.
